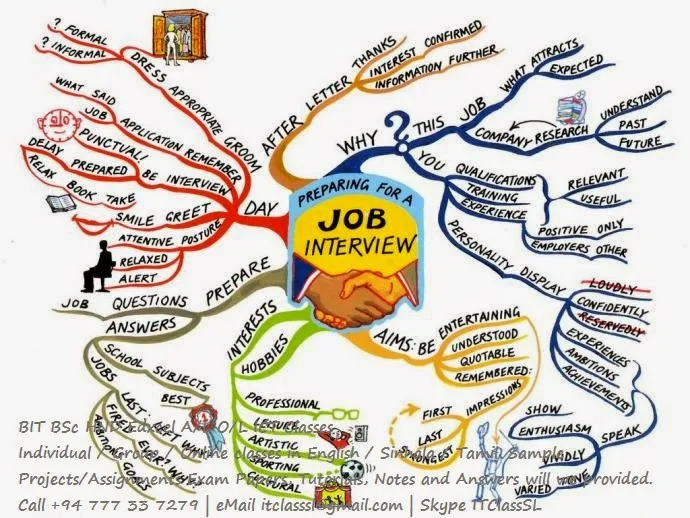
- What is PHP?
PHP is a server side scripting language commonly used for web applications. PHP has many frameworks and cms for creating websites.Even a non technical person can cretae sites using its CMS.WordPress,osCommerce are the famus CMS of php.It is also an object oriented programming language like java,C-sharp etc.It is very eazy for learning
- What is the use of "echo" in php?
It is used to print a data in the webpage, Example: <?php echo 'Car insurance'; ?> , The following code print the text in the webpage
- How to include a file to a php page?
We can include a file using "include() " or "require()" function with file path as its parameter.
- What's the difference between include and require?
If the file is not found by require(), it will cause a fatal error and halt the execution of the script. If the file is not found by include(), a warning will be issued, but execution will continue.
- require_once(), require(), include().What is difference between them?
require() includes and evaluates a specific file, while require_once() does that only if it has not been included before (on the same page). So, require_once() is recommended to use when you want to include a file where you have a lot of functions for example. This way you make sure you don't include the file more times and you will not get the "function re-declared" error.
- Differences between GET and POST methods ?
We can send 1024 bytes using GET method but POST method can transfer large amount of data and POST is the secure method than GET method .
- How to declare an array in php?
Eg : var $arr = array('apple', 'grape', 'lemon');
- What is the use of 'print' in php?
This is not actually a real function, It is a language construct. So you can use with out parentheses with its argument list.
Example print('PHP Interview questions');
print 'Job Interview ');
- What is use of in_array() function in php ?
in_array used to checks if a value exists in an array
- What is use of count() function in php ?
count() is used to count all elements in an array, or something in an object
- What’s the difference between include and require?
It’s how they handle failures. If the file is not found by require(), it will cause a fatal error and halt the execution of the script. If the file is not found by include(), a warning will be issued, but execution will continue.
- What is the difference between Session and Cookie?
The main difference between sessions and cookies is that sessions are stored on the server, and cookies are stored on the user’s computers in the text file format. Cookies can not hold multiple variables,But Session can hold multiple variables.We can set expiry for a cookie,The session only remains active as long as the browser is open.Users do not have access to the data you stored in Session,Since it is stored in the server.Session is mainly used for login/logout purpose while cookies using for user activity tracking
- How to set cookies in PHP?
Setcookie("sample", "ram", time()+3600);
- How to Retrieve a Cookie Value?
eg : echo $_COOKIE["user"];
- How to create a session? How to set a value in session ? How to Remove data from a session?
Create session : session_start();
Set value into session : $_SESSION['USER_ID']=1;
Remove data from a session : unset($_SESSION['USER_ID'];
- what types of loops exist in php?
for,while,do while and foreach (NB: You should learn its usage)
- How to create a mysql connection?
mysql_connect(servername,username,password);
- How to select a database?
mysql_select_db($db_name);
- How to execute an sql query? How to fetch its result ?
$my_qry = mysql_query("SELECT * FROM `users` WHERE `u_id`='1'; ");
$result = mysql_fetch_array($my_qry);
echo $result['First_name'];
- Write a program using while loop
$my_qry = mysql_query("SELECT * FROM `users` WHERE `u_id`='1'; ");
while($result = mysql_fetch_array($my_qry))
{
echo $result['First_name'.]."<br/>";
}
- How we can retrieve the data in the result set of MySQL using PHP?
- 1. mysql_fetch_row
- 2. mysql_fetch_array
- 3. mysql_fetch_object
- 4. mysql_fetch_assoc
- What is the use of explode() function ?
Syntax : array explode ( string $delimiter , string $string [, int $limit ] );
This function breaks a string into an array. Each of the array elements is a substring of string formed by splitting it on boundaries formed by the string delimiter.
- What is the difference between explode() and split() functions?
Split function splits string into array by regular expression. Explode splits a string into array by string.
- What is the use of mysql_real_escape_string() function?
It is used to escapes special characters in a string for use in an SQL statement
- Write down the code for save an uploaded file in php.
if ($_FILES["file"]["error"] == 0)
{
move_uploaded_file($_FILES["file"]["tmp_name"],
"upload/" . $_FILES["file"]["name"]);
echo "Stored in: " . "upload/" . $_FILES["file"]["name"];
}
- How to create a text file in php?
$filename = "/home/user/guest/newfile.txt";
$file = fopen( $filename, "w" );
if( $file == false )
{
echo ( "Error in opening new file" ); exit();
}
fwrite( $file, "This is a simple test\n" );
fclose( $file );
- How to strip whitespace (or other characters) from the beginning and end of a string ?
The trim() function removes whitespaces or other predefined characters from both sides of a string.
- What is the use of header() function in php ?
The header() function sends a raw HTTP header to a client browser.Remember that this function must be called before sending the actual out put.For example, You do not print any HTML element before using this function.
- How to redirect a page in php?
The following code can be used for it, header("Location:index.php");
- How stop the execution of a php scrip ?
exit() function is used to stop the execution of a page
- How to set a page as a home page in a php based site ?
index.php is the default name of the home page in php based sites
- How to find the length of a string?
strlen() function used to find the length of a string
- what is the use of rand() in php?
It is used to generate random numbers.If called without the arguments it returns a pseudo-random integer between 0 and getrandmax(). If you want a random number between 6 and 12 (inclusive), for example, use rand(6, 12).This function does not generate cryptographically safe values, and should not be used for cryptographic uses. If you want a cryptographically secure value, consider using openssl_random_pseudo_bytes() instead.
- what is the use of isset() in php?
This function is used to determine if a variable is set and is not NULL
- What is the difference between mysql_fetch_array() and mysql_fetch_assoc() ?
mysql_fetch_assoc function Fetch a result row as an associative array, Whilemysql_fetch_array() fetches an associative array, a numeric array, or both
- What is mean by an associative array?
Associative arrays are arrays that use string keys is called associative arrays.
- What is the importance of "method" attribute in a html form?
"method" attribute determines how to send the form-data into the server.There are two methods, get and post. The default method is get.This sends the form information by appending it on the URL.Information sent from a form with the POST method is invisible to others and has no limits on the amount of information to send.
- What is the importance of "action" attribute in a html form?
The action attribute determines where to send the form-data in the form submission.
- What is the use of "enctype" attribute in a html form?
The enctype attribute determines how the form-data should be encoded when submitting it to the server. We need to set enctype as "multipart/form-data"when we are using a form for uploading files
- How to create an array of a group of items inside an HTML form ?
We can create input fields with same name for "name" attribute with squire bracket at the end of the name of the name attribute, It passes data as an array to PHP.
For instance :
<input name="MyArray[]" /> <input name="MyArray[]" /> <input name="MyArray[]" /> <input name="MyArray[]" />
- Define Object-Oriented Methodology
Object orientation is a software/Web development methodology that is based on the modeling a real world system.An object is the core concept involved in the object orientation. An object is the copy of the real world enity.An object oriented model is a collection of objects and its inter-relationships
- How do you define a constant?
Using define() directive, like define ("MYCONSTANT",150)
- How send email using php?
To send email using PHP, you use the mail() function.This mail() function accepts 5 parameters as follows (the last 2 are optional). You need webserver, you can't send email from localhost. eg : mail($to,$subject,$message,$headers);
- How to find current date and time?
The date() function provides you with a means of retrieving the current date and time, applying the format integer parameters indicated in your script to the timestamp provided or the current local time if no timestamp is given. In simplified terms, passing a time parameter is optional - if you don't, the current timestamp will be used.
- Difference between mysql_connect and mysql_pconnect?
There is a good page in the php manual on the subject, in short mysql_pconnect() makes a persistent connection to the database which means a SQL link that do not close when the execution of your script ends. mysql_connect()provides only for the databasenewconnection while using mysql_pconnect , the function would first try to find a (persistent) link that's already open with the same host, username and password. If one is found, an identifier for it will be returned instead of opening a new connection... the connection to the SQL server will not be closed when the execution of the script ends. Instead, the link will remain open for future use.
- What is the use of "ksort" in php?
It is used for sort an array by key in reverse order.
- What is the difference between $var and $$var?
They are both variables. But $var is a variable with a fixed name. $$var is a variable who's name is stored in $var. For example, if $var contains "message", $$var is the same as $message.
- What are the encryption techniques in PHP
MD5 PHP implements the MD5 hash algorithm using the md5 function,
eg : $encrypted_text = md5 ($msg);
mcrypt_encrypt :- string mcrypt_encrypt ( string $cipher , string $key , string $data , string $mode [, string $iv ] );
Encrypts plaintext with given parameters
- What is the use of the function htmlentities?
htmlentities Convert all applicable characters to HTML entities This function is identical to htmlspecialchars() in all ways, except with htmlentities(), all characters which have HTML character entity equivalents are translated into these entities.
- How to delete a file from the system
Unlink() deletes the given file from the file system.
- How to get the value of current session id?
session_id() function returns the session id for the current session.
- What are the differences between mysql_fetch_array(), mysql_fetch_object(), mysql_fetch_row()?
- Mysql_fetch_array Fetch a result row as an associative array, a numeric array, or both.
- mysql_fetch_object ( resource result ) Returns an object with properties that correspond to the fetched row and moves the internal data pointer ahead. Returns an object with properties that correspond to the fetched row, or FALSE if there are no more rows
- mysql_fetch_row() fetches one row of data from the result associated with the specified result identifier. The row is returned as an array. Each result column is stored in an array offset, starting at offset 0.
- What are the different types of errors in PHP ?
Here are three basic types of runtime errors in PHP:
- 1. Notices: These are trivial, non-critical errors that PHP encounters while executing a script - for example, accessing a variable that has not yet been defined. By default, such errors are not displayed to the user at all - although you can change this default behavior.
- 2. Warnings: These are more serious errors - for example, attempting to include() a file which does not exist. By default, these errors are displayed to the user, but they do not result in script termination.
- 3. Fatal errors: These are critical errors - for example, instantiating an object of a non-existent class, or calling a non-existent function. These errors cause the immediate termination of the script, and PHP's default behavior is to display them to the user when they take place.
- what is sql injection ?
SQL injection is a malicious code injection technique.It exploiting SQL vulnerabilities in Web applications
- What is x+ mode in fopen() used for?
Read/Write. Creates a new file. Returns FALSE and an error if file already exists
- How to find the position of the first occurrence of a substring in a string
strpos() is used to find the position of the first occurrence of a substring in a string
- What is PEAR?
PEAR is a framework and distribution system for reusable PHP components.The project seeks to provide a structured library of code, maintain a system for distributing code and for managing code packages, and promote a standard coding style.PEAR is broken into three classes: PEAR Core Components, PEAR Packages, and PECL Packages. The Core Components include the base classes of PEAR and PEAR_Error, along with database, HTTP, logging, and e-mailing functions. The PEAR Packages include functionality providing for authentication, networking, and file system features, as well as tools for working with XML and HTML templates.
- Distinguish between urlencode and urldecode?
This method is best when encode a string to used in a query part of a url. it returns a string in which all non-alphanumeric characters except -_. have replece with a percentege(%) sign . the urldecode->Decodes url to encode string as any %and other symbole are decode by the use of the urldecode() function.
- What are the different errors in PHP?
In PHP, there are three types of runtime errors, they are:
Warnings:
These are important errors. Example: When we try to include () file which is not available. These errors are showed to the user by default but they will not result in ending the script.
Notices:
These errors are non-critical and trivial errors that come across while executing the script in PHP. Example: trying to gain access the variable which is not defined. These errors are not showed to the users by default even if the default behavior is changed.
Fatal errors:
These are critical errors. Example: instantiating an object of a class which does not exist or a non-existent function is called. These errors results in termination of the script immediately and default behavior of PHP is shown to them when they take place. Twelve different error types are used to represent these variations internally.
1. What is MySQL?
MySQL is an open source DBMS which is built, supported and distributed by MySQL AB (now acquired by Oracle)
2. What are the technical features of MySQL?
MySQL database software is a client or server system which includes
- Multithreaded SQL server supporting various client programs and libraries
- Different backend
- Wide range of application programming interfaces and
- Administrative tools.
3. Why MySQL is used?
MySQL database server is reliable, fast and very easy to use. This software can be downloaded as freeware and can be downloaded from the internet.
4. What are Heap tables?
HEAP tables are present in memory and they are used for high speed storage on temporary
basis.
• BLOB or TEXT fields are not allowed
• Only comparison operators can be used =, <,>, = >,=<
• AUTO_INCREMENT is not supported by HEAP tables
• Indexes should be NOT NULL
5. What is the default port for MySQL Server?
The default port for MySQL server is 3306.
6. What are the advantages of MySQL when compared with Oracle?
- MySQL is open source software which is available at any time and has no cost involved.
- MySQL is portable
- GUI with command prompt.
- Administration is supported using MySQL Query Browser
7. Differentiate between FLOAT and DOUBLE?
Following are differences for FLOAT and DOUBLE:
• Floating point numbers are stored in FLOAT with eight place accuracy and it has four bytes.
• Floating point numbers are stored in DOUBLE with accuracy of 18 places and it has eight bytes.
8. Differentiate CHAR_LENGTH and LENGTH?
CHAR_LENGTH is character count whereas the LENGTH is byte count. The numbers are same for Latin characters but they are different for Unicode and other encodings.
9. How to represent ENUMs and SETs internally?
ENUMs and SETs are used to represent powers of two because of storage optimizations.
10. What is the usage of ENUMs in MySQL?
ENUM is a string object used to specify set of predefined values and that can be used during table creation.
|
|
Create table size(name ENUM('Small', 'Medium','Large');
|
11. Define REGEXP?
REGEXP is a pattern match in which matches pattern anywhere in the search value.
12. Difference between CHAR and VARCHAR?
Following are the differences between CHAR and VARCHAR:
- CHAR and VARCHAR types differ in storage and retrieval
- CHAR column length is fixed to the length that is declared while creating table. The length value ranges from 1 and 255
- When CHAR values are stored then they are right padded using spaces to specific length. Trailing spaces are removed when CHAR values are retrieved.
13. Give string types available for column?
The string types are:
- SET
- BLOB
- ENUM
- CHAR
- TEXT
- VARCHAR
14. How to get current MySQL version?
is used to get the current version of MySQL.
15. What storage engines are used in MySQL?
Storage engines are called table types and data is stored in files using various techniques.
Technique involves:
- Storage mechanism
- Locking levels
- Indexing
- Capabilities and functions.
16. What are the drivers in MySQL?
Following are the drivers available in MySQL:
- PHP Driver
- JDBC Driver
- ODBC Driver
- C WRAPPER
- PYTHON Driver
- PERL Driver
- RUBY Driver
- CAP11PHP Driver
- Ado.net5.mxj
17. What does a TIMESTAMP do on UPDATE CURRENT_TIMESTAMP data type?
TIMESTAMP column is updated with Zero when the table is created. UPDATE CURRENT_TIMESTAMP modifier updates the timestamp field to current time whenever there is a change in other fields of the table.
18. What is the difference between primary key and candidate key?
Every row of a table is identified uniquely by primary key. There is only one primary key for a table.
Primary Key is also a candidate key. By common convention, candidate key can be designated as primary and which can be used for any foreign key references.
19. How do you login to MySql using Unix shell?
We can login through this command:
# [mysql dir]/bin/mysql -h hostname -u <UserName> -p <password>
20. What does myisamchk do?
It compress the MyISAM tables, which reduces their disk or memory usage.
21. How do you control the max size of a HEAP table?
Maximum size of Heal table can be controlled by MySQL config variable called max_heap_table_size.
22. What is the difference between MyISAM Static and MyISAM Dynamic?
In MyISAM static all the fields will have fixed width. The Dynamic MyISAM table will have fields like TEXT, BLOB, etc. to accommodate the data types with various lengths.
MyISAM Static would be easier to restore in case of corruption.
23. What are federated tables?
Federated tables which allow access to the tables located on other databases on other servers.
24. What, if a table has one column defined as TIMESTAMP?
Timestamp field gets the current timestamp whenever the row gets altered.
25. What happens when the column is set to AUTO INCREMENT and if you reach maximum value in the table?
It stops incrementing. Any further inserts are going to produce an error, since the key has been used already.
26. How can we find out which auto increment was assigned on Last insert?
LAST_INSERT_ID will return the last value assigned by Auto_increment and it is not required to specify the table name.
27. How can you see all indexes defined for a table?
Indexes are defined for the table by:
SHOW INDEX FROM <tablename>;
28. What do you mean by % and _ in the LIKE statement?
% corresponds to 0 or more characters, _ is exactly one character in the LIKE statement.
29. How can we convert between Unix & MySQL timestamps?
UNIX_TIMESTAMP is the command which converts from MySQL timestamp to Unix timestamp
FROM_UNIXTIME is the command which converts from Unix timestamp to MySQL timestamp.
30. What are the column comparisons operators?
The = , <>, <=, <, >=, >,<<,>>, <=>, AND, OR, or LIKE operators are used in column comparisons in SELECT statements.
31. How can we get the number of rows affected by query?
Number of rows can be obtained by
|
|
SELECT COUNT (user_id) FROM users;
|
32. Is Mysql query is case sensitive?
No.
|
|
SELECT VERSION(), CURRENT_DATE;
SeLect version(), current_date;
seleCt vErSiOn(), current_DATE;
|
All these examples are same. It is not case sensitive.
33. What is the difference between the LIKE and REGEXP operators?
LIKE and REGEXP operators are used to express with ^ and %.
|
|
SELECT * FROM employee WHERE emp_name REGEXP "^b";
SELECT * FROM employee WHERE emp_name LIKE "%b";
|
34. What is the difference between BLOB AND TEXT?
A BLOB is a binary large object that can hold a variable amount of data. There are four types of BLOB –
- TINYBLOB
- BLOB
- MEDIUMBLOB and
- LONGBLOB
They all differ only in the maximum length of the values they can hold.
A TEXT is a case-insensitive BLOB. The four TEXT types
- TINYTEXT
- TEXT
- MEDIUMTEXT and
- LONGTEXT
They all correspond to the four BLOB types and have the same maximum lengths and storage requirements.
The only difference between BLOB and TEXT types is that sorting and comparison is performed in case-sensitive for BLOB values and case-insensitive for TEXT values.
35. What is the difference between mysql_fetch_array and mysql_fetch_object?
Following are the differences between mysql_fetch_array and mysql_fetch_object:
mysql_fetch_array() -Returns a result row as an associated array or a regular array from database.
mysql_fetch_object – Returns a result row as object from database.
36. How can we run batch mode in mysql?
Following commands are used to run in batch mode:
37. Where MyISAM table will be stored and also give their formats of storage?
Each MyISAM table is stored on disk in three formats:
- The ‘.frm’ file stores the table definition
- The data file has a ‘.MYD’ (MYData) extension
- The index file has a ‘.MYI’ (MYIndex) extension
38. What are the different tables present in MySQL?
Total 5 types of tables are present:
- MyISAM
- Heap
- Merge
- INNO DB
- ISAM
MyISAM is the default storage engine as of MySQL .
39. What is ISAM?
ISAM is abbreviated as Indexed Sequential Access Method.It was developed by IBM to store and retrieve data on secondary storage systems like tapes.
40. What is InnoDB?
lnnoDB is a transaction safe storage engine developed by Innobase Oy which is a Oracle Corporation now.
41. How MySQL Optimizes DISTINCT?
DISTINCT is converted to a GROUP BY on all columns and it will be combined with ORDER BY clause.
|
|
SELECT DISTINCT t1.a FROM t1,t2 where t1.a=t2.a;
|
42. How to enter Characters as HEX Numbers?
If you want to enter characters as HEX numbers, you can enter HEX numbers with single quotes and a prefix of (X), or just prefix HEX numbers with (Ox).
A HEX number string will be automatically converted into a character string, if the expression context is a string.
43. How to display top 50 rows?
In MySql, top 50 rows are displayed by using this following query:
|
|
SELECT * FROM
LIMIT 0,50;
|
44. How many columns can be used for creating Index?
Maximum of 16 indexed columns can be created for any standard table.
45. What is the different between NOW() and CURRENT_DATE()?
NOW () command is used to show current year,month,date with hours,minutes and seconds.
CURRENT_DATE() shows current year,month and date only.
46. What are the objects can be created using CREATE statement?
Following objects are created using CREATE statement:
- DATABASE
- EVENT
- FUNCTION
- INDEX
- PROCEDURE
- TABLE
- TRIGGER
- USER
- VIEW
47. How many TRIGGERS are allowed in MySql table?
SIX triggers are allowed in MySql table. They are as follows:
- BEFORE INSERT
- AFTER INSERT
- BEFORE UPDATE
- AFTER UPDATE
- BEFORE DELETE and
- AFTER DELETE
48. What are the nonstandard string types?
Following are Non-Standard string types:
- TINYTEXT
- TEXT
- MEDIUMTEXT
- LONGTEXT
49. What are all the Common SQL Function?
CONCAT(A, B) – Concatenates two string values to create a single string output. Often used to combine two or more fields into one single field.
FORMAT(X, D) – Formats the number X to D significant digits.
CURRDATE(), CURRTIME() – Returns the current date or time.
NOW() – Returns the current date and time as one value.
MONTH(), DAY(), YEAR(), WEEK(), WEEKDAY() – Extracts the given data from a date value.
HOUR(), MINUTE(), SECOND() – Extracts the given data from a time value.
DATEDIFF(A, B) – Determines the difference between two dates and it is commonly used to calculate age
SUBTIMES(A, B) – Determines the difference between two times.
FROMDAYS(INT) – Converts an integer number of days into a date value.
50. Explain Access Control Lists.
An ACL (Access Control List) is a list of permissions that is associated with an object. This list is the basis for MySQL server’s security model and it helps in troubleshooting problems like users not being able to connect.
MySQL keeps the ACLs (also called grant tables) cached in memory. When a user tries to authenticate or run a command, MySQL checks the authentication information and permissions against the ACLs, in a predetermined order.
Ref http://career.guru99.com/top-50-mysql-interview-questions-answers/
===================================================================
Q1. What is jQuery?
Ans: jQuery is fast, lightweight and feature-rich client side JavaScript Library/Framework which helps in to traverse HTML DOM, make animations, add Ajax interaction, manipulate the page content, change the style and provide cool UI effect. It is one of the most popular client side library and as per a survey it runs on every second website.
Q2. Why do we use jQuery?
Ans: Due to following advantages.
- Easy to use and learn.
- Easily expandable.
- Cross-browser support (IE 6.0+, FF 1.5+, Safari 2.0+, Opera 9.0+)
- Easy to use for DOM manipulation and traversal.
- Large pool of built in methods.
- AJAX Capabilities.
- Methods for changing or applying CSS, creating animations.
- Event detection and handling.
- Tons of plug-ins for all kind of needs.
Q3. How JavaScript and jQuery are different?
Ans: JavaScript is a language While jQuery is a library built in the JavaScript language that helps to use the JavaScript language.
Q4. Is jQuery replacement of Java Script?
Ans: No. jQuery is not a replacement of JavaScript. jQuery is a different library which is written on top of JavaScript. jQuery is a lightweight JavaScript library that emphasizes interaction between JavaScript and HTML.
Q5. Is jQuery a library for client scripting or server scripting?
Ans. Client side scripting.
Q6. Is jQuery a W3C standard?
Ans: No. jQuery is not a W3C standard.
Q7. What is the basic need to start with jQuery?
Ans: To start with jQuery, one need to make reference of it’s library. The latest version of jQuery can be downloaded from
jQuery.com.
Q8. Which is the starting point of code execution in jQuery?
Ans: The starting point of jQuery code execution is $(document).ready() function which is executed when DOM is loaded.
Q9. What does dollar sign ($) means in jQuery?
Ans: Dollar Sign is nothing but it’s an alias for JQuery. Take a look at below jQuery code.
|
|
$(document).ready(function(){
});
|
Over here $ sign can be replaced with “jQuery” keyword.
|
|
jQuery(document).ready(function(){
});
|
Q10. Can we have multiple document.ready() function on the same page?
Ans: YES. We can have any number of document.ready() function on the same page.
Ref http://www.freshershine.com/job-tips/technical-interview/jquery-interview-questions-and-answers/
===============================================================================
1. What are different ways to apply styles to a Web page?
There are four ways to apply style to a Web page.
- Inline CSS: HTML elements may have CSS applied to them via the STYLE attribute.For Example: If You have <p> element into webpage, you can apply inline style likeshows in example.<p style=”font-size: 12px; color: #000000;”>Test </p>
- Embedded CSS: CSS may be embedded in a Web page by placing the code in a STYLE element within the HEAD element.For Example: If You have <h2> element into webpage, you can apply embedded style like shows in example.
<head>
<style type=”text/css”>
h2 {
font-size: 16px;
color: #2d2d2d;
font-weight: 900;
}
</style>
</head>
- Linked CSS: CSS can be placed in an external file (a simple text file containing CSS) and linked via the link element.You can apply style to webpage using external file as shown in example.
<link rel=”stylesheet” href=”custom/custom.css” type=”text/css” media=”screen, projection” />
- Imported CSS: Another way to utilize external CSS files via @import.<style>
@import url(‘/css/styles.css’);
</style>
Put then your “styles.css” document can contain calls to any number of additional
style sheets:
@import url(‘/css/typography.css’);
@import url(‘/css/layout.css’);
@import url(‘/css/color.css’);
2. How do CSS precedence/cascading rules work? How does the !important directive affect the rules?
CSS style rules “cascade” in the sense that they follow an order of precedence. Global style rules apply first to HTML elements, and local style rules override them. For example, a style defined in a style element in a webpage overrides a style defined in an external style sheet. Similarly, an inline style that is defined in an HTML element in the page overrides any styles that are defined for that same element elsewhere.
The !important rule is a way to make your CSS cascade but also have the rules you feel are most crucial always be applied. A rule that has the !important property will always be applied no matter where that rule appears in the CSS document. So if you wanted to make sure that a property always applied, you would add the !important property to the tag. So, to make the paragraph text always red, in the above example, you would write:
p { color: #ff0000 !important; }
p { color: #000000; }
3. What is a class? What is an ID?
A class is a style (i.e., a group of CSS attributes) that can be applied to one or more HTML elements. This means it can apply to instances of the same element or instances of different elements to which the same style can be attached. Classes are defined in CSS using a period followed by the class name. It is applied to an HTML element via the class attribute and the class name.
The following snippet shows a class defined, and then it being applied to an HTML DIV element.
.test {font-family: Helvetica; font-size: 20; background: black;}
<div class =”test”><p>test</p></div>
Also, you could define a style for all elements with a defined class. This is demonstrated with the following code that selects all P elements with the column class specified.
p.column {font-color: black;}
An ID selector is a name assigned to a specific style. In turn, it can be associated with one HTML element with the assigned ID. Within CSS, ID selectors are defined with the # character followed by the selector name.
The following snippet shows the CSS example1 defined followed by the use of an HTML element’s ID attribute, which pairs it with the CSS selector.
#example1: {background: blue;}
<div id=”example1″></div>
4. What is the difference between an ID selector and CLASS?
An ID selector identifies and sets style to only one occurrence of an element, while CLASS can be attached to any number of elements.
5. What is Contextual Selector?
Contextual selector addresses specific occurrence of an element. It is a string of individual selectors separated by white space (search pattern), where only the last element in the pattern is addressed providing it matches the specified contex
6. What is Grouping?
When more than one selector shares the same declaration, they may be grouped together via a comma-separated list; this allows you to reduce the size of the CSS (every bit and byte is important) and makes it more readable. The following snippet applies the same background to the first three heading elements.
h1, h2, h3 {background: red;}
7. What are Child Selectors?
A child selector is used when you want to match an element that is the child of another specific element. The parent and child selectors are separated by spaces. The following selector locates an unordered list element within a paragraph element and makes a text within that element bold.
p > ul {font-weight: bold;}
8. What are Pseudo Classes?
Pseudo classes allow you to identify HTML elements on characteristics (as opposed to their name or attributes). The classes are specified using a colon to separate the element name and pseudo class. A good example is the :link and :visited pseudo classes for the HTML A element. Another good example is first-child, which finds an element’s first child element.
The following CSS makes all visited links red and green, the actual link text becomes yellow when the mouse pointer is positioned over it, and the text of the first element of a paragraph is bold.
a:link {font-color: red;}
a:visited {font-color: green;}
a:hover {font-color: yellow;}
p.first-child {font-weight: bold;}
This book is far better than any other learning material. It has very basic information that includes both HTML5 and CSS3 with sample code and comprehensive examples. If you’re looking for reading material; this is a great resource.
Ref http://dglobaltech.com/css-interview-questions-and-answers-15-common-css-questions/
======================================================
What is DBMS ?
The database management system is a collection of programs that enables user to store, retrieve, update and delete information from a database.
2. What is RDBMS ?
Relational Database Management system (RDBMS) is a database management system (DBMS) that is based on the relational model. Data from relational database can be accessed or reassembled in many different ways without having to reorganize the database tables. Data from relational database can be accessed using an API , Structured Query Language (SQL).
3. What is SQL ?
Structured Query Language(SQL) is a language designed specifically for communicating with databases. SQL is an ANSI (American National Standards Institute) standard.
4. What are the different type of SQL's ?
1. DDL – Data Definition Language
DDL is used to define the structure that holds the data. For example, table.
2. DML– Data Manipulation Language
DML is used for manipulation of the data itself. Typical operations are Insert, Delete, Update and retrieving the data from the table.
3. DCL– Data Control Language
DCL is used to control the visibility of data like granting database access and set privileges to create tables etc.
5. What are the Advantages of SQL
1. SQL is not a proprietary language used by specific database vendors. Almost every major DBMS supports SQL, so learning this one language will enable programmers to interact with any database like ORACLE, SQL ,MYSQL etc.
2. SQL is easy to learn. The statements are all made up of descriptive English words, and there aren't that many of them.
3. SQL is actually a very powerful language and by using its language elements you can perform very complex and sophisticated database operations.
6. what is a field in a database ?
A field is an area within a record reserved for a specific piece of data.
Examples: Employee Name, Employee ID etc
7. What is a Record in a database ?
A record is the collection of values / fields of a specific entity: i.e. an Employee, Salary etc.